We’re in the middle of a desktop/laptop migration thanks (in-part) to the Covid pandemic and the shift to work-from-anywhere. As part of that, we have a need to include the domain user (we’re still in a hybrid deployment) in the local security group Network Configuration Operators to ensure they can manage the VPN tunnel. What sounds like a pretty straight-forward process was actually a bit of a chore to track down how to implement.
We’d been successful with using the net localgroup command to add individual users AFTER they had already logged in, but performing that step manually was certainly not maintainable, even for a small company and deployment such as ours.
Our management tooling also allowed us to complete remote configuration of the local security group, however when the configuration deployment returned as successful, inspection confirmed the user was not added.
Microsoft’s own documentation suggests to use an Intune configuration to add users to the local security groups, but it’s own tools limit the configuration to select the Network Configuration Operators group, only groups such as Administrators, something we did not want.
Admittedly we were at an inflection point where if we could not get this to work, we were looking at some serious manual work we’d need to do forever, and we weren’t that excited about it.
Ultimately I stumbled on an article by Peter Klapwijk over at inthecloud247.com. Specifically, his documented example shows how to add users to the Administrators group however a quick trial of replacing Administrators with the desired Network Configuration Operators group provided the preferred results. I’ll provide steps here to reach the same result, but I really hope you’ll head over to Peter’s site to show him some love as well. Adjust the below to comply with your own naming conventions:
- create a security group in intune: Intune Security Group
- assign users to security group (this may work with devices as well, still researching)
- create a custom configuration policy:Custom Policy
- create → platform: Windows 10 and later → profile type: Templates → Custom → Create
- Basics
- name: AddAzureGrouptoNCO
- description: Adding Laptop security group to NCO local group
- click next
- Configuration Settings
- Name: AddAzureGrouptoNCO
- description: (not required)
- OMA-URI: ./Device/Vendor/MSFT/Policy/Config/LocalUsersAndGroups/Configure
- Data type: string
- Value: (example)
- click next
- Scope tags → click next
- Assignments
- Add groups → use the group created in step 1
- click next
- Applicability rules → click next
- Review & Create → click create
<GroupConfiguration>
<accessgroup desc = "Network Configuration Operators">
<group action = "U"/>
<add member = "AzureAD\gambit"/>
</accessgroup>
</GroupConfiguration>
When done, you can view the configuration and it should resemble this
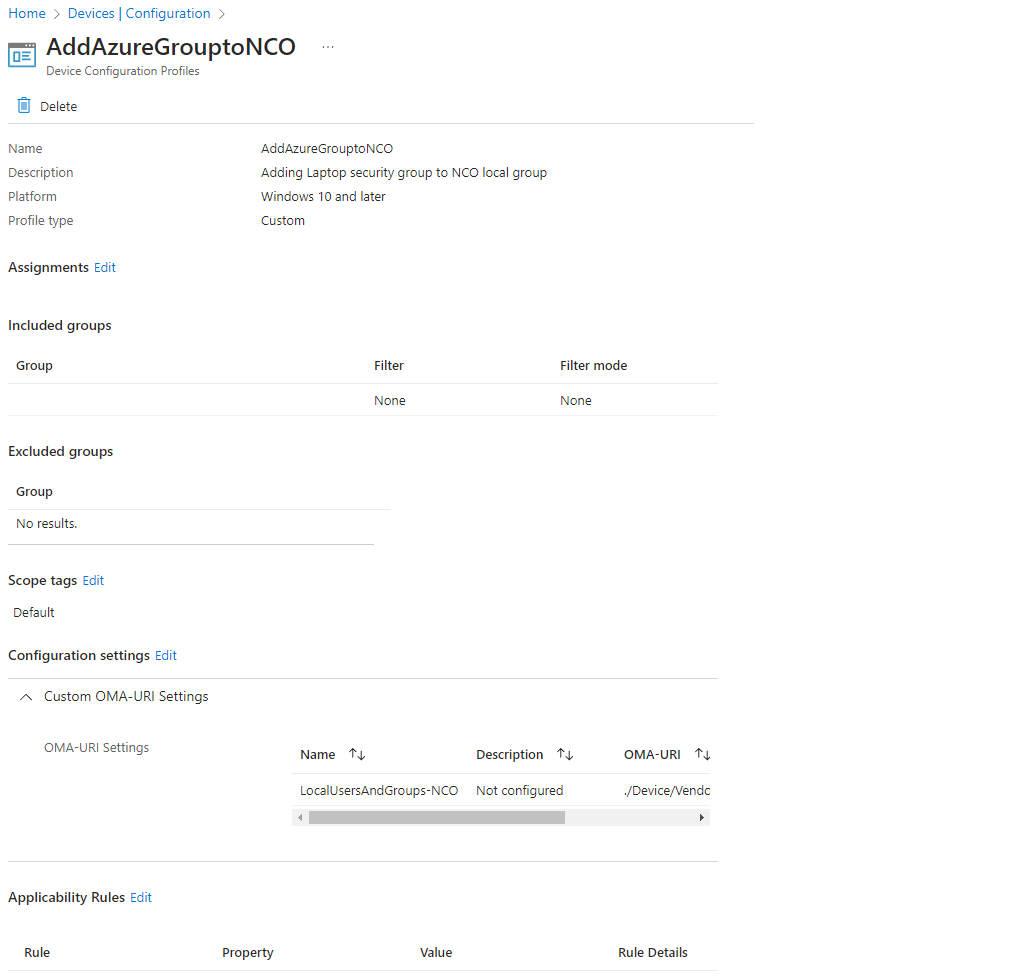
When a user of the assigned security group signs in, they will pull down the configuration script which is then applied to the local security policy. The end result is the local security group now reflects the domain user:
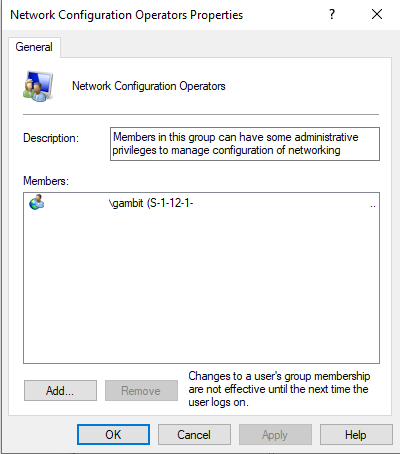
I truly hope this helps someone else in the future. The documentation surrounding this is thorough but perhaps not as intuitive for some of us that are not full time O365/M365 admins. Again I encourage you to visit’s Peter’s site, referenced above, for a very detailed walk through. Hopefully this tl;dr version will get you through to the desired results.
Cheers,